What's New, Halcyon? Enterprise Web UI January 2024 Release Notes


Halcyon is pleased to announce the availability of the Enterprise Web UI. The new Enterprise Web UI can be accessed at preview.halcyon.ai alongside the existing UI that will still be available at manage.halcyon.ai until further notice.
Halcyon will be releasing new Enterprise Web UI functionality iteratively over the coming weeks. Customers can tentatively expect future functionality to be released as follows and, of course, existing functionality improvements will come with these iterations as well:
- Iteration 3.4 - Data Export - January
- Iteration 3.5 - Alert Mutability - February
- Iteration 3.6 - Audit Log - February
- Iteration 3.7 - Artifacts - March
- Iteration 3.8 - Events - March
- Iteration 3.9 - Tasks and Dashboard - April
Customers who have enabled SSO for existing UI access will be able to authenticate to the Enterprise Web UI using the same credentials.
What's New
The Halcyon Enterprise Web UI is a new platform designed to deliver richer details covering Agent health, alert analysis, and deeper visibility and control of the Halcyon deployment including policy control and data export (coming end of January).
Alerts Screen
The Alerts screen provides an enhanced and holistic view of alerts reported by all assets. It serves as a consolidated summary of all alerts for a given tenant, offering a unified perspective for both Block (Active Mode) and Warning (Learning Mode) alerts in a single aggregated view.
- Level includes Block for Active Mode and Warning for Learning Mode
- Type includes Bad Behavior and Malicious Executable:
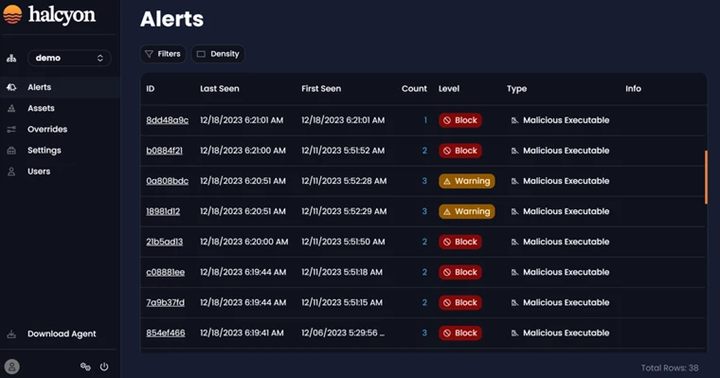
Alerts Screen
New Filters for Alerts Management
After selecting Filter dropdown, users gain access to a set of new filtering options Last Seen, First Seen, Count, Level and Type:
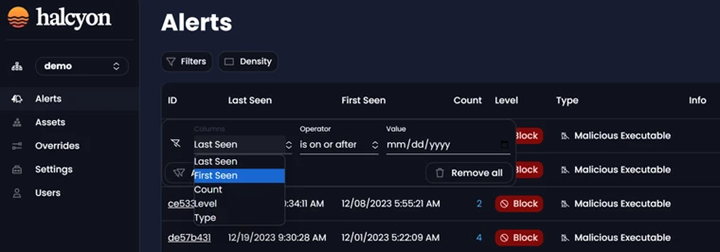
Alerts Filters
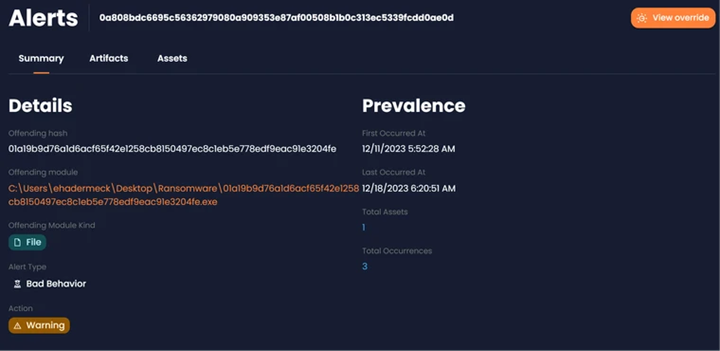
Ability to view Detail Alerts
After clicking on an Alert ID, users can view more details of an alert. The Summary tab will include Alert Details along with information on its prevalence, specifying when and how many occurrences have been recorded:
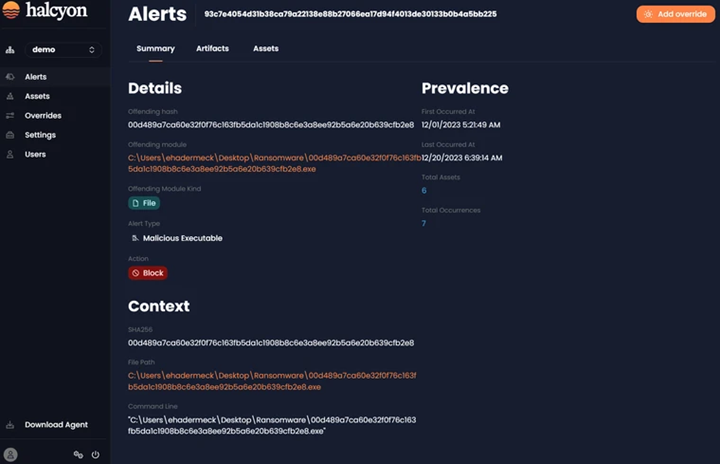
Alert Summary Tab
The Artifacts tab provide the detailed information, including the hash, path and the kind of threat:
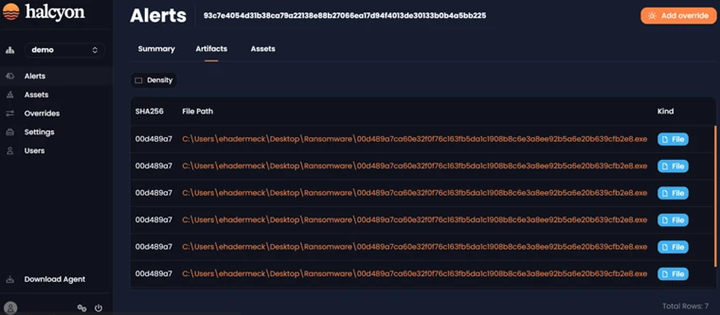
Alert Artifacts Tab
The Assets tab will display the assets where alert occurred:
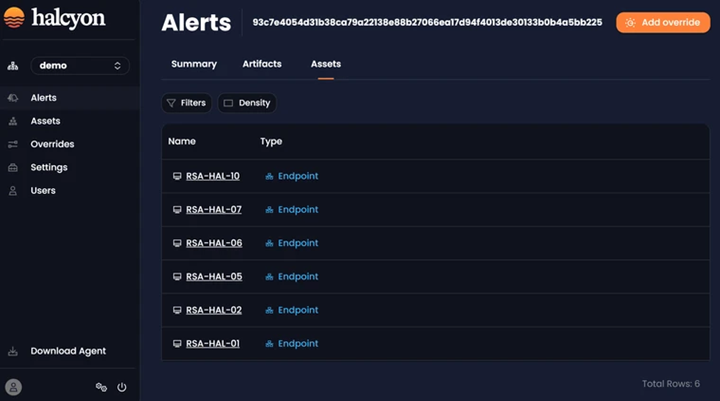
Alert Assets Tab
Ability to Add/Remove Override
In the detailed Alert view, if a user deems an alert to be safe, they can click on "Add override" button on the top right corner to allow it. Conversely, if they change their decision, they can click on “View override” button and then click "Remove override" to revoke the allowance:

Add Override
View Override
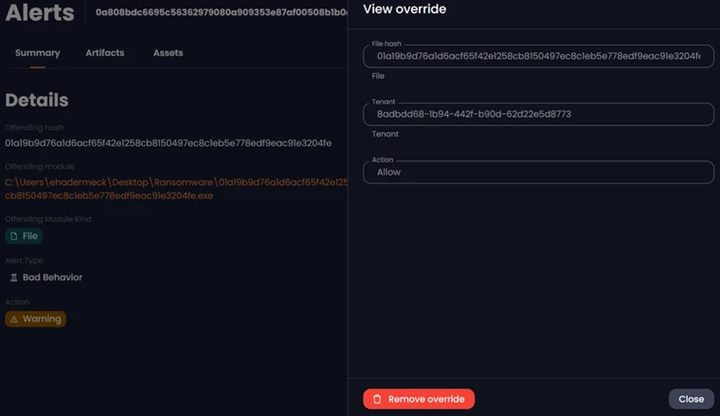
Remove Override
Assets Screen
The Assets screen, formerly referred to as Devices, showcases the organization's managed assets along with their corresponding threat information. The new Assets Screen includes additional filters and sorting abilities:

Assets Screen
New Filters for Assets Management
After selecting Filter dropdown, users will encounter a set of new filtering options, including Name, Agent version, OS Name and Type:
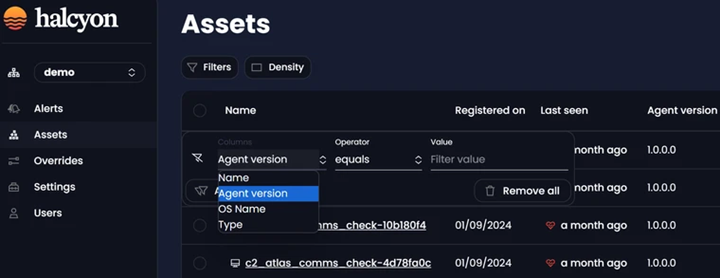
Assets Filters
Ability to View Detail Asset Info
After clicking on a selected Asset Name, users can access detailed information pertaining to the selected asset. The Agent Info tab provides essential details about the selected asset's HAR Agent, including its name, version, and the date of the last update:
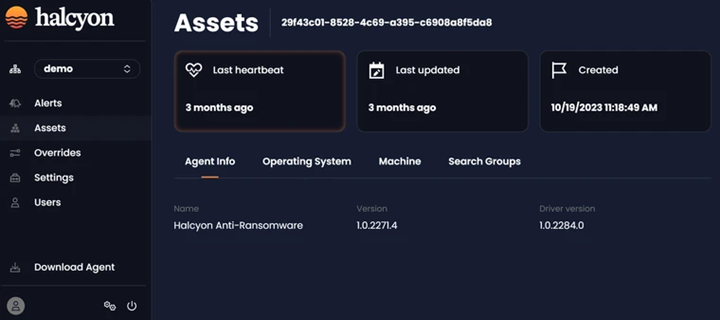
Agent Info Tab
The Operating System tab presents detail information about the operating system (OS) installed on the selected asset:
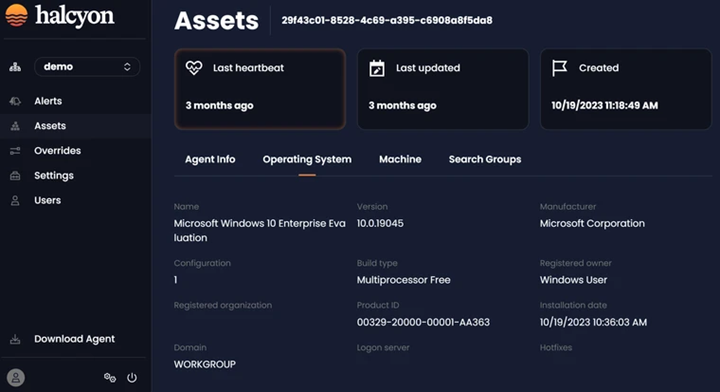
Operating System Tab
The Machine tab includes detail information of the selected asset:
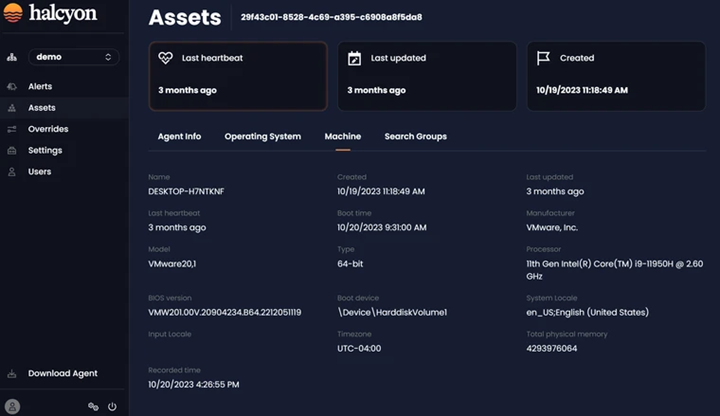
Machine Tab
The Search Groups tab enables users to efficiently manage and categorize assets through grouping (formerly known as tagging):
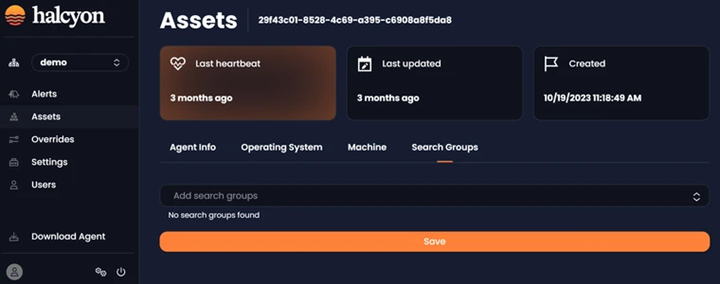
Search Groups Tab
Override Screen
The Overrides screen enables users to view and manage rules that override default behaviors and actions triggered by identified threats. There are 3 types of overrides: Certificates, Hash and Monitor.
The Certificates tab enables users create and edit overrides for specific certificates by providing the thumbprint. Users can choose the Target at either the Asset level (specific assets) or Tenant level (all assets in a specific tenant) and define the desired Action (Allow or Block). Files signed with a certificate thumbprint listed in the overrides will be processed based on the specified Action:
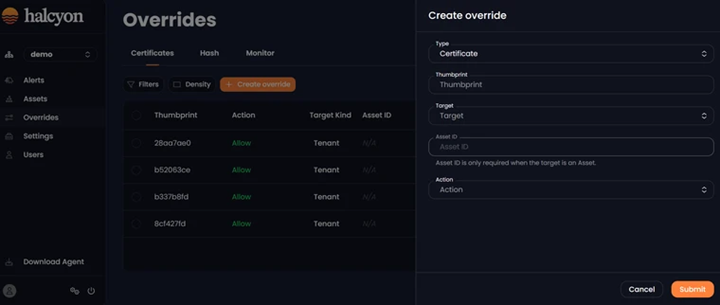
Overrides - Certificates Tab
The Hash tab enables users create and edit overrides for specific files by providing the file hash/SHA256. Users can choose the Target at either the Asset level (specific assets) or Tenant level (all assets in a specific tenant) and define the desired Action (Allow or Block):
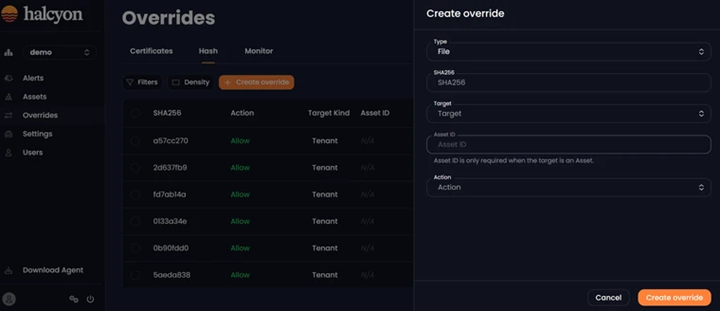
Overrides - Hash Tab
The Monitor tab enables users create and edit overrides for specific files by providing the file hash/SHA256. Users can choose the Target at either the Asset level (specific assets) or Tenant level (all assets in a specific tenant) and define the desired Action (Bypass Only):
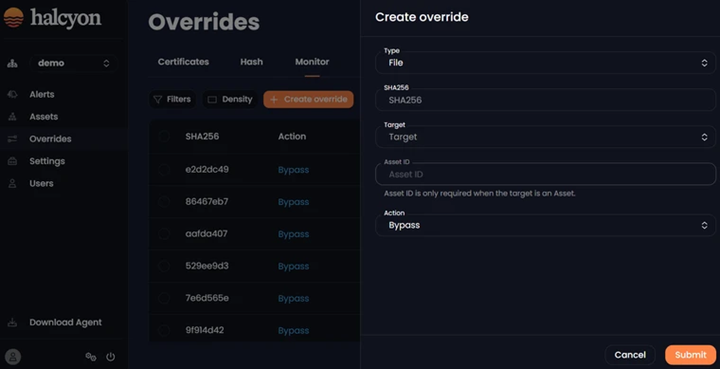
Overrides - Monitor Tab
Halcyon.ai is the leading anti-ransomware company. Global 2000 companies rely on the Halcyon platform to fill endpoint protection gaps and defeat ransomware with minimal business disruption through built-in bypass and evasion protection, key material capture, automated decryption, and data exfiltration and extortion prevention – talk to a Halcyon expert today to find out more. Halcyon also publishes a quarterly RaaS and extortion group reference guide, Power Rankings: Ransomware Malicious Quartile, and check out the Recent Ransomware Attacks resource site.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





