Halcyon Threat Insights 019: August 2025 Ransomware Report


NOTE: Every month get the latest ransomware news and analysis from the Halcyon RISE Team - join us for the next Threat Insights webinar (or watch on-demand here): https://t.co/4hYSwyNUPk
Here are the key insights from the Halcyon Rise Team (Research, Intelligence, Services, Engineering) based on intelligence collected from our customer base throughout July 2025. The evolving ransomware landscape continues to reveal intriguing trends when analyzed comprehensively:
Threats Prevented by Industry Vertical
The Manufacturing, Retail, and Government sectors were the most targeted industry verticals in June 2025:
Threat Types by Category
Halcyon detected and blocked a wide variety of threats in client environments that were missed by other security solutions:
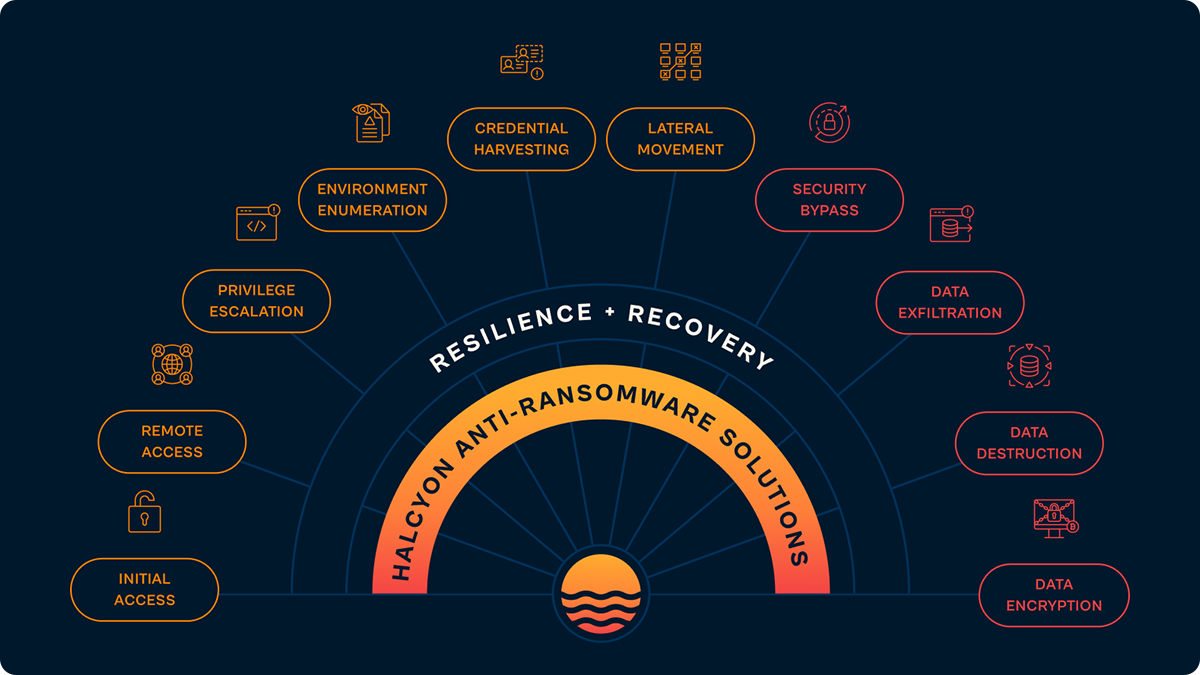
July Detections
Halcyon detects a range of behaviors and tooling at every stage of the ransomware attack chain from initial access through privilege escalation and lateralization to the final encryption payload. The following are just a few examples of detections from July 2025:
Initial Access
- Trojan.turtleloader/fxxav (VT Score 46): A modular loader that uses three specialized techniques to stage and execute secondary payloads while avoiding detection. It employs shellcode to dynamically resolve download and execution APIs at runtime, eliminating static references that could reveal its purpose. It reads configuration values, payload locations, and execution parameters directly from the Windows registry, allowing operators to change behavior without modifying the binary. It also exploits DLL sideloading by planting a malicious DLL next to a trusted, signed application, ensuring the legitimate process loads the attacker’s code. These methods allow TurtleLoader to bypass conventional detection and maintain operational flexibility. The malware has been used to deliver Cobalt Strike beacons, facilitate lateral movement, and prepare environments for ransomware deployment. Its design enables rapid adaptation to target-specific requirements and supports sustained control of compromised systems, making it a preferred loader in precision intrusion campaigns that demand stealth and resilience.
Remote Access
- Hacktool.ammyy/ammyyadmin (VT Score 46): A modified version of the legitimate Ammyy Admin remote administration software, repurposed to provide covert remote access and control over targeted systems. Attackers use the tool’s built-in encrypted communication and stealth execution capabilities to operate without raising user suspicion. The altered binary disables or bypasses consent prompts, hides the application window, and can run entirely in the background. It enables full desktop viewing, file transfer, process manipulation, and system configuration changes, effectively functioning as a lightweight remote access trojan under the guise of legitimate software. The compromised build can be configured to connect automatically to attacker-controlled servers, often without visible indicators on the host. Because it retains the signed components and core functionality of the original software, it can evade casual inspection and some security controls. This makes it a preferred tool for maintaining persistent, interactive access in targeted environments while blending in as a trusted application.
Privilege Escalation
- Trojan.shellcoderunner/goshell (VT Score 50): A loader implemented in Go that executes embedded or retrieved shellcode directly in memory to deploy follow-on payloads without touching disk. It allocates executable memory regions, copies the shellcode into them, and transfers execution to bypass standard process creation and file-based detection mechanisms. GoShell can dynamically resolve API functions needed for memory allocation, privilege escalation, and network communication, avoiding static imports that could reveal its capabilities. It supports encrypted or obfuscated shellcode payloads, decoding them at runtime to frustrate analysis. The loader can be configured to inject the shellcode into remote processes or run it within its own address space, enabling flexible deployment strategies. Its architecture allows operators to rapidly swap or update payloads without rebuilding the loader. This combination of in-memory execution, dynamic API resolution, and process injection makes GoShell an effective tool for delivering advanced post-exploitation frameworks, credential theft modules, or ransomware staging components.
Environment Enumeration
- Pua.adfind (VT Score 25): A command-line Active Directory enumeration tool often repurposed in intrusion campaigns for reconnaissance. It queries domain controllers to extract detailed directory information, including organizational units, group memberships, trust relationships, and user account attributes. AdFind can also identify domain controllers, network topology, and system objects, providing attackers with a comprehensive map of the environment. Its lightweight executable and lack of dependencies allow it to run without installation, often blending in as a legitimate administrative utility. Operators frequently pair AdFind with custom scripts to automate data harvesting and feed results into privilege escalation or lateral movement workflows. Because it relies on native LDAP queries and standard domain protocols, its activity may appear normal in network logs unless carefully monitored. When integrated into an intrusion chain, AdFind enables precise targeting of high-value accounts and systems, setting the stage for subsequent credential abuse, domain dominance, and deployment of follow-on attack payloads.
Credential Harvesting
- Trojan.msil/jalapeno (VT Score 57): A .NET-based loader designed to deliver and execute additional malicious payloads while evading detection and facilitating credential harvesting. It typically stores its secondary payload in an obfuscated or encrypted form within the binary or retrieves it from a remote server at runtime. Jalapeno decrypts and injects the payload directly into memory, bypassing disk-based scanning and minimizing forensic artifacts. It uses reflection and dynamic assembly loading to execute malicious code without creating traditional process structures, complicating analysis and avoiding some endpoint monitoring. The loader can deploy credential harvesting modules to collect passwords, tokens, and authentication data from browsers, memory, or local security stores before exfiltrating them to remote infrastructure. It may also implement anti-analysis techniques such as debugger checks, control flow obfuscation, and delayed execution to hinder detection during sandbox evaluation. Its modular design allows operators to rapidly update payloads, change command-and-control endpoints, or alter delivery methods without modifying the core loader. This adaptability, combined with in-memory execution, dynamic loading, and credential harvesting capabilities, makes Jalapeno an effective staging component for advanced campaigns involving lateral movement or ransomware deployment.
- Trojan.risepro/strictor (VT Score 58): A credential-stealing malware variant designed to harvest sensitive information from compromised systems and exfiltrate it to attacker-controlled infrastructure. It targets a wide range of data sources, including browser-stored credentials, autofill data, cryptocurrency wallet files, and authentication tokens from desktop applications. Strictor scans the file system for predefined paths and extensions associated with valuable data, then packages the collected information into compressed archives for transmission. It can capture system fingerprints, network configuration details, and hardware identifiers to support victim profiling and facilitate follow-on targeting. The malware uses obfuscation and packing to evade static detection, with runtime decryption of its core components to hinder reverse engineering. Communication with its command-and-control servers is often encrypted, obscuring the stolen data in transit. This combination of broad data theft capabilities, evasion techniques, and secure exfiltration channels makes RisePro.Strictor an efficient tool for monetizing access and enabling further compromise of affected environments.
- Trojan.gpbj/qrrqm (VT Score 27): A loader that executes secondary payloads entirely in memory to avoid leaving artifacts on disk and to facilitate credential harvesting. It allocates executable memory regions, writes embedded or downloaded payloads into them, and transfers execution control while bypassing conventional process creation mechanisms. QRRQM uses dynamic API resolution to call critical Windows functions for memory management, credential dumping, privilege escalation, and network operations without including static imports that could be flagged during scanning. It can decrypt or unpack payloads at runtime, enabling operators to update or swap malicious modules without altering the loader’s base code. The malware supports process injection into trusted applications, allowing malicious activity to run under legitimate process names and avoid scrutiny. Its in-memory execution model, combined with obfuscation, runtime decryption, and credential harvesting capabilities, makes QRRQM effective for deploying post-exploitation frameworks, data theft utilities, or ransomware staging components while minimizing forensic evidence and reducing the likelihood of detection by traditional file-based security solutions.
Lateral Movement
- Hacktool.inveigh/msil (VT Score 50): A .NET-based network attack framework designed for conducting man-in-the-middle, credential capture, and lateral movement operations within Windows environments. It emulates core features of tools like Responder and SMBTrap, enabling interception of authentication attempts over protocols such as LLMNR, NBNS, and MDNS. Inveigh can spoof legitimate network services to coerce systems into sending authentication hashes, which it then captures for offline cracking, pass-the-hash attacks, or immediate use in authenticated sessions to move between systems. It supports HTTP/HTTPS and SMB challenge–response interception, NTLM relay attacks, and can log detailed authentication events for operational planning. The framework’s modular design allows operators to selectively enable features, adjust spoofing behavior, and tailor output formats for integration with other attack tools. Execution in PowerShell or as a compiled binary provides flexibility for persistence and evasion. By operating over standard Windows networking protocols and without always requiring elevated privileges, Inveigh can blend into normal traffic while systematically harvesting credentials and enabling the movement of an attacker across networked systems in targeted environments.
Security Bypass
- Trojan.gojg/agentb (VT Score 33): Trojan.GOJG/AgentB is a loader leveraged in ransomware operations with a primary focus on bypassing security controls to deliver high-impact payloads. It executes secondary malware entirely in memory, avoiding disk-based artifacts that traditional antivirus tools scan for. The loader allocates executable memory regions, writes an embedded or remotely retrieved ransomware component into those regions, and transfers execution control without spawning new processes that might trigger endpoint detection. Dynamic API resolution is used to obtain Windows function addresses for memory manipulation, process injection, and privilege escalation only at runtime, reducing the static footprint. AgentB can inject ransomware payloads into trusted system processes, allowing malicious activity to appear as legitimate operations and evade application whitelisting. Runtime decryption enables operators to update ransomware modules without modifying the loader itself. This combination of stealth techniques, in-memory execution, and process masquerading makes AgentB highly effective for initiating ransomware attacks while bypassing conventional security defenses.
- Trojan.msil/shelm (VT Score 51): A .NET-based loader designed to deploy additional malicious payloads using in-memory execution to evade file-based detection. It stores its secondary payload in an encrypted or obfuscated format within the binary or retrieves it from a remote source at runtime, decrypting and executing it directly in allocated memory. Shelm employs reflection and dynamic assembly loading to run malicious code without creating conventional process artifacts, complicating both detection and forensic analysis. It can incorporate anti-analysis measures such as control flow obfuscation, debugger checks, and delayed execution to avoid sandbox detection. The loader’s modular structure allows operators to quickly modify payloads, alter command-and-control infrastructure, or adjust loading techniques without changing the main executable. This flexibility, combined with its in-memory execution and stealth-focused design, makes Shelm an adaptable component for campaigns delivering post-exploitation frameworks, credential theft tools, or ransomware staging modules while maintaining a minimal forensic footprint.
- Trojan.heavensgate/r002c0ded24 (VT Score 39): A loader that uses the HeavensGate technique to execute 64-bit shellcode from within a 32-bit process, bypassing security products and analysis tools that focus on a single architecture. By switching the CPU execution context from 32-bit to 64-bit mode inside the same process, it can interact directly with 64-bit APIs while retaining the appearance of a 32-bit process, allowing it to evade certain monitoring and policy restrictions. The loader allocates executable memory, writes its payload—either embedded or retrieved from a remote server—into that region, and transfers control without creating new processes or leaving disk-based artifacts. It employs dynamic API resolution to obscure functionality, resolving Windows functions for memory manipulation, privilege escalation, and process injection only at runtime to minimize its detection surface. Payloads can be encrypted or compressed, with unpacking and decryption performed entirely in memory. This architecture provides a robust means of defeating both static and behavioral detection mechanisms while enabling the delivery of post-exploitation frameworks, credential theft utilities, or ransomware staging components in environments with strict security controls.
- Trojan.vsntef25 (VT Score 23): A loader designed to execute secondary payloads entirely in memory to avoid generating disk-based artifacts and to evade common security controls. It allocates executable memory regions, writes its embedded or remotely retrieved payload into those regions, and transfers control without spawning new processes that might trigger behavioral monitoring. The malware employs dynamic API resolution to retrieve Windows function addresses for memory management, process injection, and network communication only at runtime, reducing static detection signatures. It can decrypt or unpack payloads in memory, allowing operators to swap or update malicious modules without recompiling the loader. VSNTEF25 can inject into trusted processes to blend execution under legitimate names, bypassing application whitelisting and some EDR process inspection. Its design supports rapid adaptation for varied operational needs, making it well-suited for deploying post-exploitation frameworks, credential theft utilities, or ransomware staging components while minimizing forensic traces, defeating signature-based scanning, and complicating detection by conventional endpoint protection systems.
Data Exfiltration
- Hacktool.ngrok/nettool (VT Score 25): A repurposed build of the legitimate Ngrok tunneling utility configured to provide covert external access to internal network services and facilitate data exfiltration. It establishes encrypted tunnels from a compromised host to attacker-controlled endpoints, bypassing firewall restrictions and NAT by routing traffic through Ngrok’s relay infrastructure. Operators can expose local HTTP, RDP, SSH, or custom ports without opening inbound connections on the victim network, enabling remote control, bulk data transfer, or staging of further attacks. The modified or preconfigured version can automatically connect to predefined tunnel endpoints upon execution, often without displaying a console or requiring user interaction. Because it uses legitimate infrastructure and encrypted communications over standard ports, its traffic can blend into normal network activity and evade perimeter defenses. This makes Ngrok.NetTool an effective post-compromise utility for maintaining persistent access, extracting sensitive information, and supporting operations that require concealed, bidirectional communication with systems inside protected environments.
Data Destruction
- Powershell Command Vssadmin.exe: A legitimate Windows command-line utility used for managing the Volume Shadow Copy Service, which creates and maintains shadow copies of volumes for backup and restore purposes. In malicious operations, threat actors frequently abuse vssadmin.exe to erase shadow copies and disable related features, preventing recovery of encrypted or deleted files. Common attacker commands include vssadmin delete shadows /all /quiet to silently remove all snapshots and vssadmin resize shadowstorage to restrict or break shadow copy functionality. Because it is a signed Microsoft binary residing in C:\Windows\System32, its execution often bypasses application control policies and blends in with administrative activity. When invoked during ransomware or destructive campaigns, vssadmin.exe is typically run early in the attack chain to ensure that local backups are unusable, increasing the likelihood of ransom payment or permanent data loss. Monitoring its use, especially with deletion or resize arguments, is critical for detecting and disrupting such activity.
Data Encryption
- Trojan.aqiqw/filerepmalware (VT Score 46): A loader designed to execute malicious payloads directly in memory, minimizing forensic artifacts and bypassing file-based detection. It allocates executable memory space, writes its embedded or remotely retrieved payload into that space, and transfers control without creating new processes. The malware uses dynamic API resolution to call required Windows functions for memory allocation, process injection, and network operations only at runtime, obscuring its capabilities from static analysis. Payloads are often encrypted or packed, with decryption and unpacking performed entirely in memory to hinder reverse engineering. Aqiqw.FileRepMalware can inject into trusted processes to disguise its activity and maintain persistence, while its modular structure allows rapid payload swapping without recompiling the loader. These traits make it an adaptable staging mechanism for deploying post-exploitation frameworks, credential theft modules, or ransomware components, enabling stealthy and flexible intrusion operations that are difficult to detect and analyze using conventional security tools.
- Trojan.hjau/themida (VT Score 55): A malicious payload protected with the Themida software protection and packing framework to hinder analysis and evade detection. Themida applies advanced virtualization, code obfuscation, and anti-debugging techniques, making reverse engineering and static analysis significantly more difficult. The loader decrypts or unpacks its malicious components only at runtime, executing them directly in memory to avoid leaving artifacts on disk. It uses dynamic API resolution to call required Windows functions for memory management, process injection, and network communication without including static imports. The packed payload may include additional anti-analysis features such as debugger detection, environment checks, and execution delays to bypass sandbox evaluation. By combining in-memory execution with heavy code obfuscation, HJAU.Themida conceals both its loader functionality and the capabilities of its embedded malware. This approach enables threat actors to deploy post-exploitation frameworks, credential theft tools, or ransomware components while significantly increasing the time and resources required for defenders to analyze and respond.
- Ransomware.lockbit/lockbit2 (VT Score 68): A second-generation variant of the LockBit ransomware family, engineered for rapid encryption and automated propagation in targeted environments. It uses a highly optimized multi-threaded encryption routine, allowing it to lock large volumes of files in minimal time while selectively avoiding critical system directories to maintain operational stability until ransom demands are issued. The payload can disable security tools, delete shadow copies, and terminate processes that may interfere with encryption. LockBit2 employs a hybrid cryptographic scheme, combining symmetric encryption for speed with asymmetric encryption for securing keys, preventing victims from decrypting data without the attacker’s private key. It supports configurable ransom notes, network-wide deployment through stolen domain credentials, and optional data exfiltration for double extortion. The malware is modular, allowing affiliates to tailor targeting, propagation methods, and ransom instructions. Its efficiency, automation, and customization make LockBit2 a preferred choice in high-volume, high-impact ransomware campaigns.
Threat Actor Spotlight: Interlock Ransomware
Interlock has rapidly evolved into a technically sophisticated and highly disruptive ransomware operation since first emerging in late 2023. The group quickly gained notoriety through a series of destructive attacks that blend custom tooling with aggressive data extortion tactics and operational discipline.
Interlock operates as a closed, non-public affiliate model, requiring trusted referrals and maintaining tight control over affiliate access and operational scope. Within its first year, Interlock has been linked to more than 60 confirmed intrusions, reflecting a growing pace and calculated expansion strategy.
Although not directly tied to any prior ransomware brand, Interlock’s attack structure, tool usage, and emphasis on recovery sabotage bear striking similarities to legacy groups such as BlackCat/ALPHV and LockBit. These similarities include the use of partial encryption to accelerate impact, as well as deliberate targeting of backup and recovery infrastructure.
Initial access is most often obtained through stolen credentials purchased from Initial Access Brokers (IABs) or collected through credential harvesting campaigns. Once inside, Interlock uses a mix of custom loaders and obfuscated PowerShell scripts to deploy its ransomware payload across hybrid Windows and Linux environments with minimal detection.
A recent investigation in the DFIR Report uncovered a new version of the Interlock Remote Access Trojan (RAT), used by the ransomware group known as Interlock or NodeSnake. This updated version is written in PHP instead of JavaScript or Node.js, making it stealthier and more evasive against security tools.
Interlock encrypts data using AES encryption, with RSA used for key protection. Interlock's toolset includes known credential theft utilities such as Mimikatz, along with customized tools that inject into legitimate processes, disable endpoint protections, and evade debugging and analysis tools.
The group aggressively disables recovery capabilities by deleting shadow copies, halting backup agents, and tampering with system restore mechanisms. Persistence is maintained through scheduled tasks, registry changes, and abuse of built-in Windows features, allowing access to survive reboots and remediation attempts. This modular and evasive framework enables rapid compromise and long-term access within victim networks.
Victims span a broad range of sectors including professional services, education, manufacturing, healthcare, and retail, with operations tracked in North America, Europe, and parts of Asia. The group’s opportunistic targeting suggests a focus on organizations that possess sensitive data and may be vulnerable to public exposure or prolonged operational downtime.
Interlock maintains a structured RaaS arrangement in which affiliates typically retain 70 to 80 percent of ransom proceeds, while the core team takes a smaller share. Consistent with other modern ransomware groups, Interlock employs double extortion by exfiltrating sensitive data prior to encryption and hosting victim data on leak sites to pressure for payment.
Since its debut, Interlock has steadily escalated its pace, now linked to more than 80 confirmed ransomware incidents. The group’s growing reach and refined tactics suggest a maturing operation with an expanding footprint. While exact ransom figures are not always disclosed, available reports suggest Interlock customizes demands based on victim profile, with requests ranging from hundreds of thousands to several million dollars.
Through a combination of custom-developed tools, deliberate targeting strategies, and a flexible delivery framework, Interlock has quickly become one of the most capable and dangerous ransomware operations currently active. Check out the most recent advisory on Interlock from the FBI and CISA.
Learn more about the leading ransomware threat actors by consulting the Halcyon quarterly RaaS (Ransomware as a Service) and extortion group reference guide, Power Rankings: Ransomware Malicious Quartile, and check out the Halcyon Attacks Lookout resource site.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





