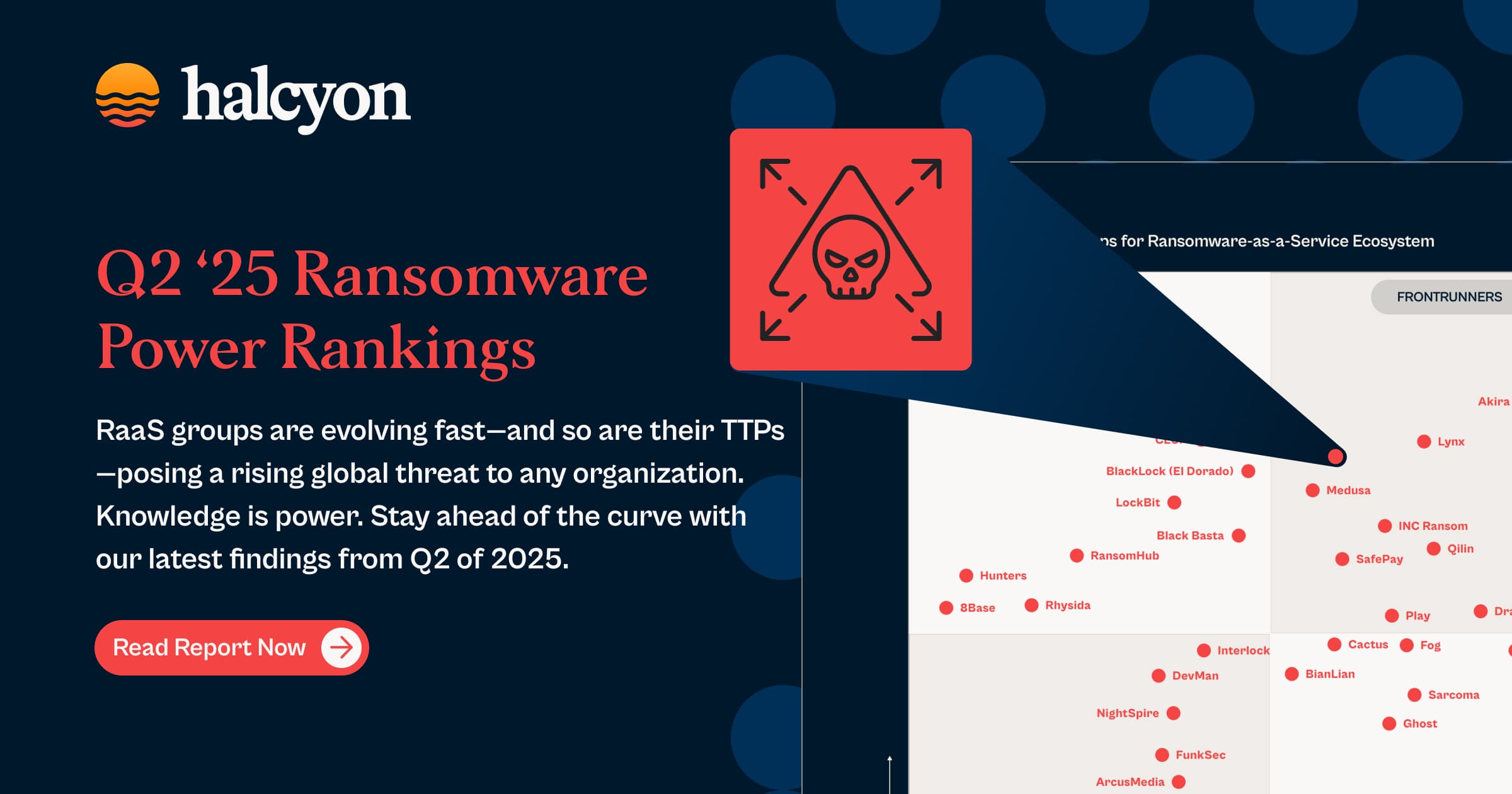
Power Rankings: Q2-2025 Ransomware Malicious Quartile

Ransomware remains one of the most destructive and expensive threats facing organizations today. With average ransom demands hitting $3.5M, victims are forced into high-stakes decisions under intense pressure: pay up or risk catastrophic disruption.
Nearly half of all targeted organizations end up paying, even after negotiations. The impact doesn’t end with encryption: recovery takes weeks, services stall, regulators circle, and trust erodes. Ransomware isn’t just a cybersecurity problem; it’s a full-blown operational crisis.
The Halcyon team of ransomware experts has put together this extortion group power rankings guide as a quick reference for the extortion threat landscape based on data from throughout Q2-2025, which can be reviewed along with earlier reports here: Power Rankings: Ransomware Malicious Quartile.
Halcyon Tracked ransomware groups actively compromising organizations between April and June 2025, noting a slight increase from the prior quarter. Since our last report:
Major Movements:
- New Leader: DragonForce was the only group added to the Leaders Quartile in Q2, following its expansion into new regions and adoption of advanced techniques like BYOVD.
- Removed: RansomHouse and DarkVault were removed entirely from the Q2 report due to inactivity.
- New Additions: Interlock, DevMan, NightSpire, FunkSec, and RALord (Nova) were added to the Q2 report as emerging groups show early operational momentum.
- Former Leaders in Decline: Once top-tier actors, Cl0p, RansomHub, LockBit, BlackBasta, and 8Base all dropped from the Leaders quartile in Q2—taken down by law enforcement, internal collapse, or fading affiliate trust.
Evolution of Tactics, Techniques, and Procedures:
- Security Bypass: DragonForce is now using BYOVD to bypass kernel defenses, while others rely on intermittent encryption to slip past EDR.
- Virtual Infrastructure Under Siege: Ransomware crews like Qilin and Medusa are aggressively targeting VMware ESXi with custom payloads built for virtualized environments.
- Living Off the Land Remotely: Threat actors like Sarcoma and others are abusing legitimate RMM tools for stealthy recon and lateral movement, blending in with IT traffic to extend dwell time undetected.
- Smarter Payloads, Smarter Theft: Threat actors like Akira, Qilin, Arcus Media, and DevMan are consolidating tools, harvesting browser-stored credentials, and deploying modular ransomware frameworks purpose-built for speed, stealth, and disruption.
The ransomware threat landscape continues to evolve at a breakneck pace with established groups collapsing under pressure while new operations rise fast with sharper tools and smarter tactics.
The Q2-2025 shift shows that no ransomware brand stays dominant for long, but the business model remains brutally effective. Organizations must stay ahead of these shifts, because the next headline-making attack won’t come from the usual suspects.
Check out the full report here: Power Rankings: Ransomware Malicious Quartile
Halcyon eliminates the business impact of ransomware. Modern enterprises rely on Halcyon to prevent ransomware attacks, eradicating cybercriminals’ ability to encrypt systems, steal data, and extort companies – talk to a Halcyon expert today to find out more, and check out our quarterly RaaS and extortion group reference guide, Power Rankings: Ransomware Malicious Quartile.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





.jpg)
