Halcyon Threat Insights 003: March 2024


Here are the key insights from the Halcyon Threat Research and Intelligence Team findings for March 2024. The evolving ransomware landscape continues to reveal intriguing trends when analyzed comprehensively.
Ransomware Prevented per Industry Vertical
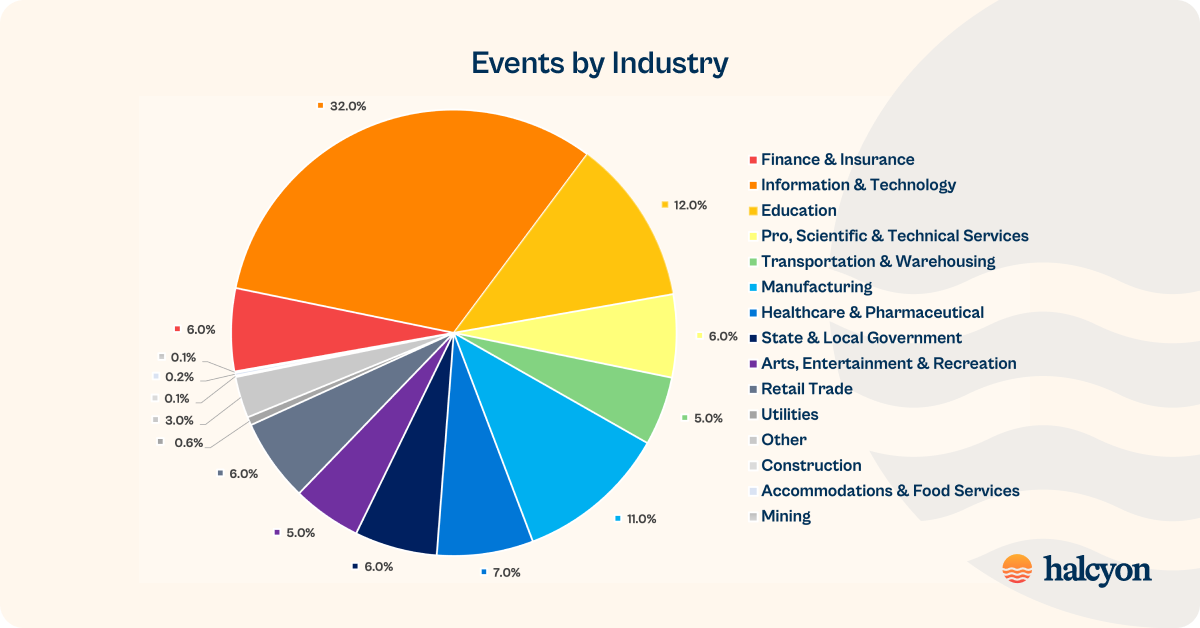
Information Technology, Education and Manufacturing were the most targeted industry verticals in March 2024:
- Information & Technology 32% (+13% mo/mo)
- Education 12% (-1% mo/mo)
- Manufacturing 11% (+6% mo/mo)
- Healthcare & Pharmaceutical 7% (+3% mo/mo)
- Finance & Insurance 6% (-25%% mo/mo)
- Professional, Scientific & Technical Services 6% (-2% mo/mo)
- State & Local Government 6% (+2% mo/mo)
- Retail Trade 6% (+4% mo/mo)
- Arts, Entertainment & Recreation 5%
- Transportation & Warehousing 5% (+2% mo/mo)
- other 3% (+2% mo/mo)
- Utilities 0.6% (-0.4% mo/mo)
- Accommodations & Food Services 0.2% (-0.1% mo/mo)
- Construction 0.1% (-0.3% mo/mo)
- Mining 0.1% (-0.2% mo/mo)
Threat Types by Category

Halcyon detected and blocked a wide variety of threats that were missed by other security layers in our client’s environments that are often precursors to the delivery of the ransomware payload:
Monero Coin Miner Trojan
This Trojan installs a Monero coin miner, effectively stealing processing resources from the victim and is capable of performing various evasion techniques to avoid detection and analysis by security tools.
This Trojan connects to the URL hXXp://185.172.128.11/zima.php?mine=XMR to download and execute additional payloads through a dynamic loading that injects code into other processes, allowing it to evade detection by traditional antivirus products.
This Trojan also injects PE files into other processes, which can be used to execute arbitrary code on the infected system and has been observed encrypting its communications and payloads using AES (Advanced Encryption Standard) along with uses evasion techniques such as sleeping the process.
ClipBanker Trojan
This sophisticated malware targets sensitive information, particularly focusing on cryptocurrency transactions. It operates by monitoring the Windows clipboard for manipulating or stealing data, including currency-related information.
The malware employs various methods to infiltrate systems, often masquerading as legitimate cryptocurrency applications or being installed via Trojan droppers. Once inside, ClipBanker attempts to evade detection by whitelisting itself in common antivirus software, making it a stealthy and dangerous threat to infected machines.
Hacktool.msil/sharphound
SharpHound is designed to collect various types of data from an AD environment, such as group memberships, session information, and trust relationships, which can then be used by BloodHound to visualize and analyze the security posture of the AD environment.
Trojan.convagent/r002c0wki21
Trojan.convagent are a family droppers used to install other malware variants and typically employed in click-fraud schemes. While click-fraud is a nuisance, this family also has some capabilities that could be employed for more nefarious means, including recording user keystrokes, collecting information about infected devices, and possibly allowing remote access.
Trojan.installcore
Tool is used to automate the detection and exploitation of command injection vulnerabilities. It is typically leveraged to install other malware variants often employed in click-fraud schemes. This family can also record user keystrokes, collect information about infected devices, and allow remote access.
Trojan.imrux/python
This trojan can drop and execute files with high VT scores. This and similar trojan/python instances can be difficult to determine whether it is malicious or not, as homebrewed scripts and other unsigned programs bundled into .exe files can trigger false positives in antivirus software.
Threat Actor Spotlight: Akira
Akira first emerged in March 2023, and the group may have links to the notorious Conti gang, although this is difficult to ascertain given the Conti code was leaked in 2022.
Akira operations include data exfiltration for double extortion with the threat to expose or sell the data should the victim fail to come to terms with the attackers and is assessed to have leaked gigabytes of stolen data from victims.
Interestingly, Akira’s extortion platform includes a chat feature for victims to negotiate directly with the attackers, and it has been observed that Akira will inform victims who have paid a ransom of the infection vectors they leveraged to carry out the attack. This is not ransomware “standard procedure” as many ransomware operators have engaged in multiple attacks on the same victim leveraging the same vulnerabilities.
Akira operates a RaaS written in C++ that is capable of targeting both Windows and Linux systems, typically by exploiting credentials for VPNs. Akira modules will delete Windows Shadow Volume Copies leveraging PowerShell and is designed to encrypt a wide range of file types while avoiding Windows system files with .exe, .lnk, .dll, .msi, and .sys extensions. Akira also abuses legitimate LOLBins/COTS tools like PCHunter64, making detection more difficult.
In July 2023, a Linux variant for Akira was detected in the wild, and the group was also observed remotely exploiting a zero-day in Cisco’s Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software (CVE-2023-20269) in brute-force attacks since at least August. Akira has also been observed exploiting VMware ESXi vulnerabilities for lateral movement.
Akira maintains a modest but growing attack volume, putting them in about the middle of the pack when compared to other ransomware operators. Ransom demands appear to range between $200,000 to more than $4 million. The group has attacked dozens of organizations across multiple industry verticals including education, finance, and manufacturing.
Akira maintains a modest but growing attack volume, putting them in about the middle of the pack when compared to other ransomware operators. Ransom demands appear to range between $200,000 to more than $4 million.
Learn more about the leading ransomware threat actors by consulting the Halcyon quarterly RaaS (Ransomware as a Service) and extortion group reference guide, Power Rankings: Ransomware Malicious Quartile, and check out the Recent Ransomware Attacks resource site.
Halcyon.ai is the leading anti-ransomware company. Global 2000 companies rely on the Halcyon platform defeat ransomware with minimal business disruption through built-in bypass and evasion protection, key material capture, automated decryption, and data exfiltration and extortion prevention – talk to a Halcyon expert today to find out more.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





