Halcyon Threat Insights 001: January 2024


The following are high-level findings from the Halcyon Threat Research and Intelligence team discovered during Q4-2023. As always with shifting ransomware landscape, there are some interesting trends that can be uncovered with enough data.
Threats Blocked by Industry Vertical
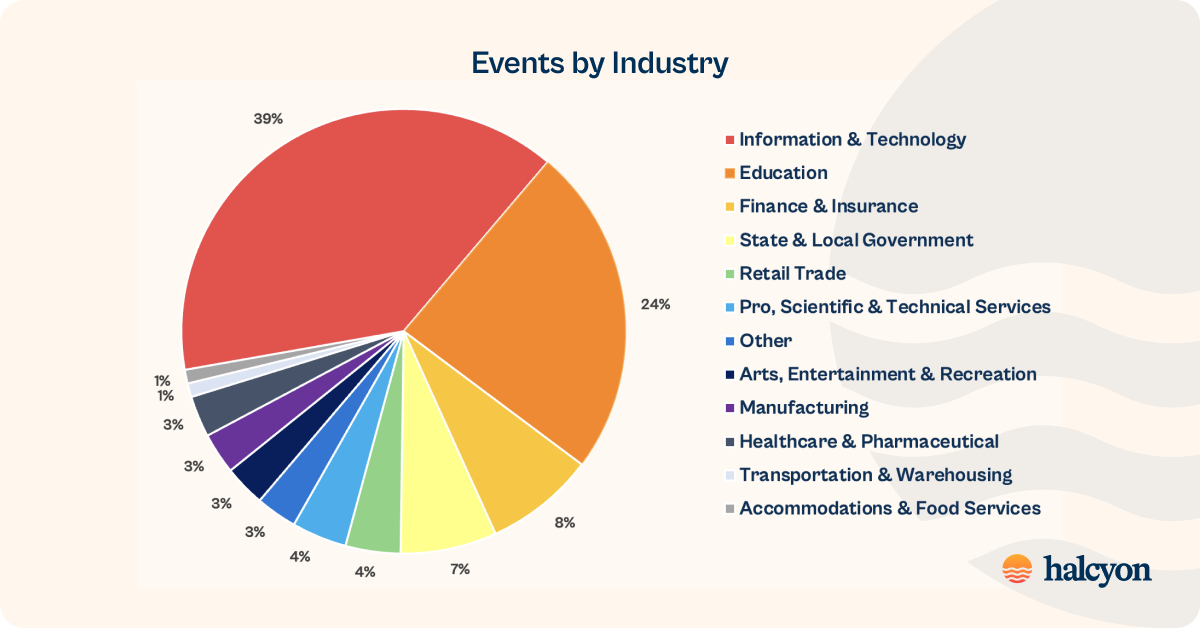
IT, Education and Financial organizations were the most targeted industry verticals in the fourth quarter of 2023:
- Information & Technology: 39%
- Education: 24%
- Finance & Insurance: 8%
- State & Local Government: 7%
- Retail Trade: 4%
- Professional, Scientific & Technical Services: 4%
- Other: 3%
- Arts, Entertainment & Recreation: 3%
- Manufacturing: 3%
- Healthcare & Pharmaceutical: 3%
- Transportation & Warehousing: 1%
- Accommodations & Food Services: <1%
Blocking Misconfiguration Exploits
Halcyon detected and blocked a C# tool designed for enumerating and exploiting misconfigurations in Active Directory Certificate Services called GhostPack Certify. This tool can potentially exploit vulnerabilities in the certificate infrastructure, leading to unauthorized access and potential data breaches.
If Certify were allowed to operate unchecked, it could have resulted in significant security breaches within the Active Directory environment, compromising sensitive data and the integrity of our systems.
Detecting Stealthy Malware
We also successfully blocked multiple instances of the Babar Trojan, a highly sophisticated and stealthy malware strain known for harvesting credentials and exfiltrating data.
Babar establishes persistence through registry keys, scheduled tasks, or service entries. Babar provides attackers with remote access, keylogging, execution of commands, and lateral movement within the network.
Babar also manipulates data or settings, employs security evasion techniques, self-propagates across networks, communicates with command-and-control servers (C2), and delivers malicious payloads, making it a formidable threat.
Penetration Testing Coverage
As an enterprise security vendor, our tools commonly pick up signals from internal red team tooling and breach and attack simulation products.
These activities included running tools regularly abused by ransomware operators, including Mimikatz, SharpHound, DueDLLigence, GoShell, Convagent and others commonly associated with credential theft, information gathering, and whitelisting bypasses.
While we encourage routine security product testing, organizations should remember that these testing tools and techniques do not always accurately represent what is seen in a real-world attack.
We picked up multiple attempts to execute the QakBot trojan, an advanced banking Trojan designed to steal sensitive financial information, keylogging, network traffic interception, and deploying additional malicious payloads.
The Halcyon Anti-Ransomware Platform detected and blocked these threats even as the other EDR and EPP products deployed on the endpoints did not. Our ability to detect and analyze the usage of tools associated with credential theft, information gathering, and application whitelist bypasses underscores our expertise in identifying exploitable vulnerabilities.
Case Study in Brief
In 2023, a manufacturing company with revenues nearing $1B annually was attacked by the Akira ransomware group. Akira encrypted all Windows workstations and servers halting their business and operations. All backups were destroyed and were not recoverable.
The company feared they would need to rebuild all their systems from scratch which would require multiple technology partners and take months to complete at great cost to the organization. But by partnering with Halcyon, the company and their incident response provider were able to quickly restore their most critical assets and resume operations.
Halcyon immediately restored 90% of file shares, 95% of critical server infrastructure, and nearly all local files impacted by the attack. Halcyon then expelled the attackers from the network to ensure a secure operating environment.
Halcyon accomplished this without the need to pay the attackers a ransom, without capturing an encryption key, and without the need for costly remediation approaches like the re-imaging of every impacted device.
The company has now deployed Halcyon across their entire network and has not experienced any disruptions from subsequent ransomware attacks. Learn more about the Halcyon Services Portfolio by contacting services@halcyon.ai.
Halcyon.ai is the leading anti-ransomware company. Global 2000 companies rely on the Halcyon platform to fill endpoint protection gaps and defeat ransomware with minimal business disruption through built-in bypass and evasion protection, key material capture, automated decryption, and data exfiltration and extortion prevention – talk to a Halcyon expert today to find out more. Halcyon also publishes a quarterly RaaS (Ransomware as a Service) and extortion group reference guide, Power Rankings: Ransomware Malicious Quartile, and check out the Recent Ransomware Attacks resource site.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





