Rhysida ransomware emerged in May 2023 as a Ransomware-as-a-Service (RaaS) operation, initially establishing itself through high-impact attacks on critical infrastructure sectors. Operating under the moniker "Rhysida-0.1", the group demonstrated technical proficiency with RSA-4096 and ChaCha20 encryption, rapidly targeting organizations where operational disruption creates maximum leverage. The group notably lacks a full-featured victim support portal common among more mature RaaS operations, relying instead on basic TOR-based communication channels. Recent intelligence indicates significant operational changes, with activity declining substantially from late 2024 into 2025, suggesting disruption from the February 2024 free decryptor release and a marked reduction in operational prominence.
Despite reduced volume, the group maintains persistent targeting of healthcare and education sectors, leveraging double extortion tactics with ransom demands typically ranging from hundreds of thousands to several million dollars. The group's infrastructure has evolved to include multi-tiered command-and-control (C2) systems and cross-platform capabilities with Linux/ESXi variants, though overall operational tempo suggests a group experiencing significant transition rather than expansion.
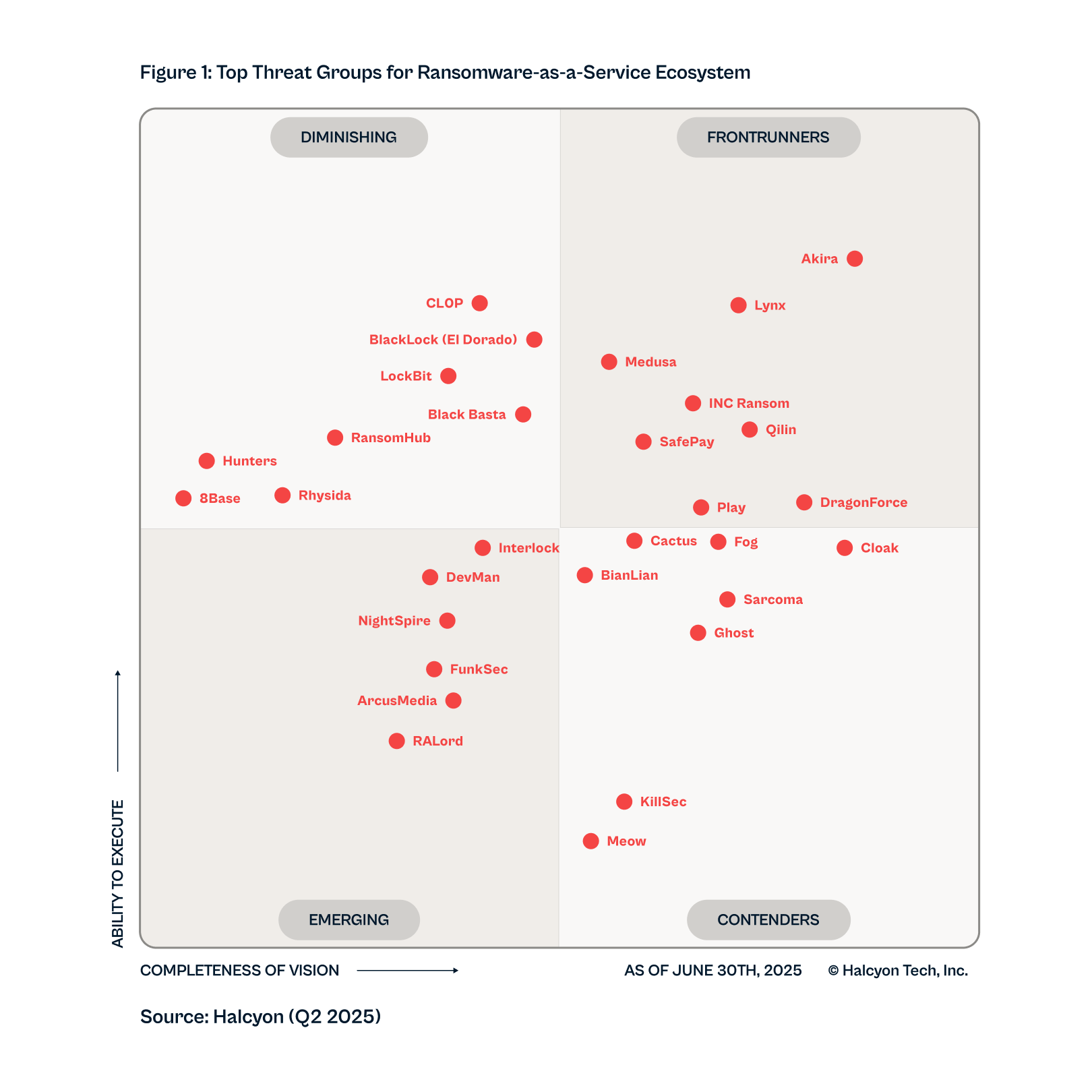


.png)

.webp)





