EXPOSING YOUR RANSOMWARE adversaries
Threat Actor Index: Knowledge is Power
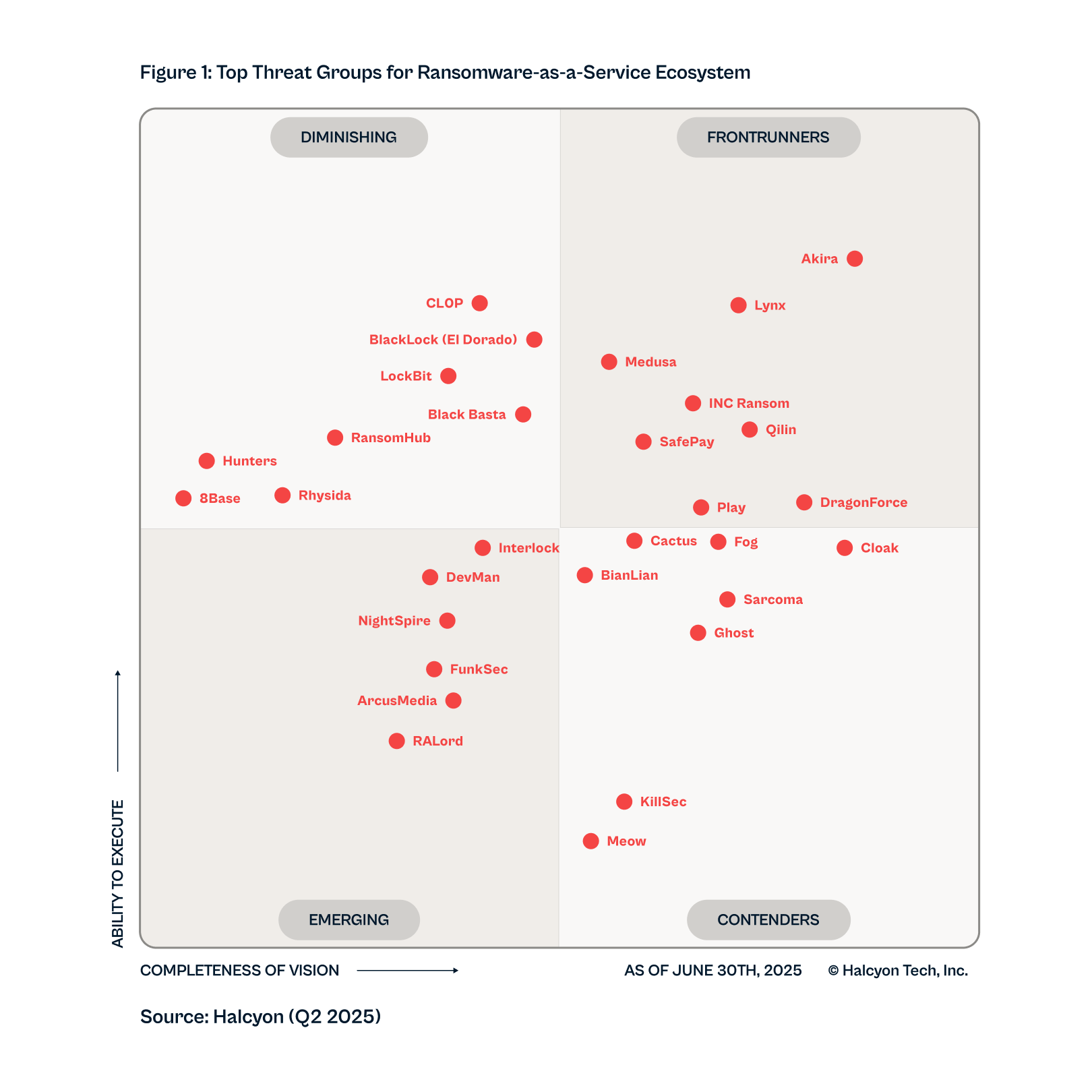
Welcome to the Halcyon Ransomware Threat Actor Index, a comprehensive catalog of the most prominent threat actors and ransomware families, to shed light on the ransomware ecosystem. Discover their techniques, tactics, procedures and targeted industries. Make informed decisions, and stay resilient in the face of ransomware.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


.png)

.webp)





