Ransomware Roundup: 08.28.23


Snatch Ransomware Gang Adds Cyber Insurance Twist on Double Extortion
The Snatch ransomware gang appears to be putting a new twist on the double extortion gambit: giving cyber insurers details of how they infected victims in order to nullify coverage if those victims refuse to pay the ransom demand.
Double extortion is a very common tactic used by ransomware gangs to compel victims to pay a ransom demand. Variations include data exfiltration with the threat to expose or sell the data, threats to notify the victim’s customers their data has been breached, denial of service (DoS) attack threats, and more.
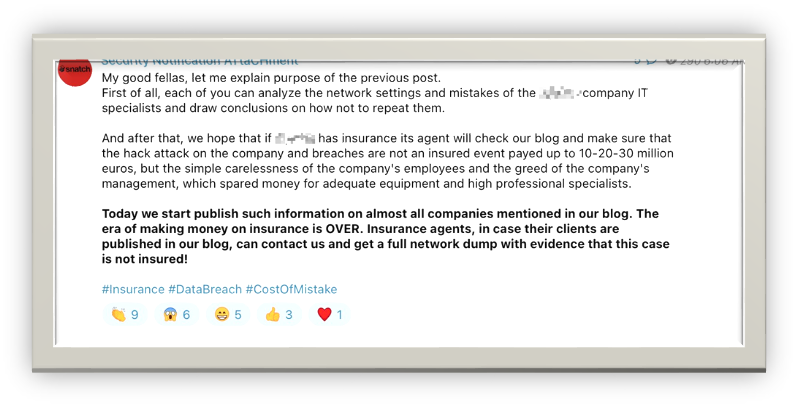
Snatch Extortion Note – Credit: Bret Callow
Threat actors began using double extortion tactics to counter a victim’s ability to restore systems and data from backups or other means of recovery that do not include paying the attackers in order to receive a decryption key.
Takeaway: The threat to expose infection vectors and provide details to cyber insurers if victims fail to pay is yet another clever twist on the double extortion tactic and could put victims in a tricky situation when considering the best course of action following a successful ransomware attack.
For example, if a victim organization did decide to pay a ransom because they believe that the attack details would invalidate their insurance converge, they could be putting themselves in legal jeopardy for withholding material information from their insurer and from stakeholders.
This isn’t the first time a ransomware gang has tried to leverage insurers by putting victim organizations in an ethical and legal tight spot: back in March, the HardBit began instructing victims to provide details of their cyber insurance coverage so the attackers can properly set the ransom demand.
“The hackers tell victims to anonymously provide them with the details of their cyber insurance <sic> so that they can set the ransom amount accordingly,” SecurityWeek reported.
“The HardBit operators say they do not want to demand more than what the victim can recover from the insurance company, but they also don’t want to be offered a low amount by the insurer’s representatives.”
Victim organizations should keep in mind that even good-faith negotiations with ransomware attackers to set an amount and terms for payment could face intense scrutiny by their insurer, by law enforcement, and by regulators.
Furthermore, any payment to ransomware operators who may be under international sanctions restrictions could land an organization and its leadership in very serious trouble.
No organization should ever entertain any offer of collusion with attackers. By doing so they would expose their organizations to a degree of legal jeopardy that simply is not worth contemplating.
Left of Boom: Developing Ransomware Early Warning Systems
In March of 2022, the Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA) established the Ransomware Vulnerability Warning Pilot (RVWP) program in an effort to warn critical infrastructure operators of vulnerabilities known to be exploited by ransomware threat actors.
“As part of RVWP, CISA leverages existing authorities and technology to proactively identify information systems that contain security vulnerabilities commonly associated with ransomware attacks,” CISA states.
“Once CISA identifies these affected systems, our regional cybersecurity personnel notify system owners of their security vulnerabilities, thus enabling timely mitigation before damaging intrusions occur.”
In a similar manner, the United Kingdom’s security and intelligence services have developed the Early Warning program, which is administered by the National Cyber Security Centre (NCSC - part of GCHQ) to warn organizations of early-stage ransomware attacks before they become serious security incidents.
“The experts have built a unique system using the intelligence community’s access to several information feeds unavailable to anyone else — alongside public, commercial and closed-source inputs — that has almost certainly prevented a significant number of ransomware attacks,” The Record reported.
Takeaway: Early detection of attacks can mean the difference between an attempted ransomware attack versus a full-blown incident response and recovery process that can take weeks to months to complete and cost an organization tens of millions of dollars in losses.
There are many players in the Ransomware Economy, from the RaaS platform providers who provide the ransomware attack tooling, to the affiliates who select targets and carry out the attacks, to the money launderers who obfuscate the money trail when victims pay a ransom.
Halcyon researchers recently identified another major player in the Ransomware Economy: Command-and-Control Providers (C2P) who lease the attack infrastructure to threat actors, in a report titled Cloudzy with a Chance of Ransomware: Unmasking Command-and-Control Providers (C2Ps) (PDF).
While these C2P entities are ostensibly legitimate businesses that may or may not know that their platforms are being abused for attack campaigns, they nonetheless provide a key pillar of the larger attack apparatus leveraged by some of the most advanced threat actors.
In this report, Halcyon demonstrates a unique method for identifying C2P entities that can potentially be used to forecast the precursors of ransomware campaigns and other attacks significantly “left of boom.”
Halcyon used an unlikely pivot point – namely RDP hostnames within the metadata of an affiliate’s attack infrastructure – to detect imminent ransomware and nation-state sponsored attacks as the infrastructure is being stood up, providing notice weeks to months before the attack is launched.
Halcyon researchers successfully used this technique to identify a C2P called Cloudzy that provided attack infrastructure to APT groups tied to the Chinese, Iranian, North Korean, Russian, Indian, Pakistani, and Vietnamese governments; to a sanctioned Israeli spyware vendor whose tools are known to target civilians; and to several criminal syndicates and ransomware affiliates whose campaigns have spurred international headlines.
Halcyon began with a large set of previously published and undisclosed ransomware attack network IOCs. Using Internet scanning data from Censys and Shodan, we noticed what seemed to be a group of RDP hostnames recurring frequently within the “Subject Common Name” field of X.509 certificates.
These SSL certificates were most frequently used to secure RDP connections on the default TCP port, 3389. By default, Windows sets the “Subject Common Name” field to match the server’s hostname when first issuing SSL certificates for RDP.
Halcyon linked RDP hostnames to ransomware incidents by connecting the SSL certificates where the hostnames appeared to associated IP addresses which matched the known TTPs of ransomware groups we track.
Halcyon noted that several of these RDP hostnames were also called out as indicators of compromise (IOCs) in ransomware incidents by several different security researchers. This served to confirm our initial findings that these RDP hostnames were associated with malicious infrastructure used in ransomware campaigns.
Halcyon then determined that the IP addresses associated with the SSL certificates containing these hostnames were also connected to one another based upon their distribution over multiple Internet Service Providers (ISPs).
Halcyon did not expect to find the same hostnames repeated so often across so many different providers. The fact that they did suggest to us that someone had used an imaging process to quickly copy and then widely deploy servers across them.
Halcyon examined the broader IP space associated with the SSL certificates containing those RDP hostnames, conducting PDNS analysis within a 90-day window of the RDP hostnames first appearing. We did this to limit the likelihood of any IP-based crossover.
What Halcyon discovered was a staggering array of attack infrastructure which we, and others in the security community, recognized and associated with a wide range of threat actors. Included were government-sponsored APT groups, criminal syndicates, and a commercial spyware vendor.
Halcyon researchers pioneered a new technique that can enable defenders to spot malicious hostnames proactively to identify potential threats as the attack infrastructure is being set up. Hopefully these and other efforts to provide better visibility into immanent threats can help protect organizations from catastrophic attacks earlier in the initial attack sequence.
While we will never be able to stop ransomware attacks, we can stop them from being successful by making actionable intelligence available that can be used to end an attack earlier.
Attack Takes Critical Mississippi Hospital System Services Offline
Singing River Health System, which operates several major regional hospitals and clinics, was forced to take numerous systems offline following a suspected ransomware attack.
Singing River Health System serves more than 100,000 patients per year, and a spokesperson said patients can expect delays on some medical services including radiology examinations, lab work, and potentially more, as “all systems are currently offline,” the spokesperson told The Record.
“Downtime procedures remain in place as we continue to see patients. We are working very hard to provide more definitive information regarding what systems will be available and when. Our IT security team is working around the clock, but due to the nature of this matter, this will take some time,” the spokesperson said.
“Certain internal SRHS systems were taken offline to protect the integrity of the systems during the investigation. SRHS is working to restore offline systems. We developed workaround solutions to enable a portion of our business operations to continue while we complete a thorough investigation.”
Takeaway: Ransomware attacks are one of the biggest threats facing every organization, and healthcare providers have been hit particularly hard.
Earlier this month, a ransomware attack disrupted healthcare systems in California, Texas, Connecticut, Rhode Island and Pennsylvania, forcing the suspension of services at emergency rooms and causing ambulances to be diverted to other facilities. The attacks have also caused the suspension of primary care services.
Ransomware operators know that the impact of an attack against healthcare organizations doesn’t just disrupt everyday business, it directly affects the lives of their patients, which puts tremendous pressure on the targeted provider to pay up for swift recovery
Healthcare providers are a favorite target for ransomware operators given they typically have fewer resources to dedicate to security, the networks are often composed of older legacy components, and any downtime is extremely disruptive.
The average time it takes for an organization to recover from a ransomware attack has been pegged at about three weeks or more according to multiple studies. While a private, profitable organization with ample resources may be able to weather such a lengthy disruption to operations, the healthcare game is one of immediacy.
Patients are different than customers, and in most cases, they cannot afford delays in treatment without putting their health at risk.
There is no way to argue against the fact that ransomware attacks on healthcare providers pose a significant threat to human life. While the perception is that the industry must be flush with cash given how expensive healthcare is to obtain, it is a misconception.
The reality is that our nation’s healthcare system is for the most part operated by non-profit entities who work on shoestring margins. Disruptive ransomware attacks are an existential threat to healthcare and put patients’ lives at risk.
New BlackCat/ALPHV Ransomware Variant Abuses Impacket and RemCom Tools
Microsoft researchers uncovered a new BlackCat/ALPHV ransomware variant that embeds Impacket and RemCom tools for lateral movement and remote code execution.
"The Impacket tool has credential dumping and remote service execution modules that could be used for broad deployment of the BlackCat ransomware in target environments," The Hacker News reports.
"This BlackCat version also has the RemCom hacktool embedded in the executable for remote code execution. The file also contains hardcoded compromised target credentials that actors use for lateral movement and further ransomware deployment."
Takeaway: BlackCat/ALPHV is arguably the most advanced ransomware threat in the wild, as noted in our report Power Rankings: 2022 Ransomware Malicious Quartile.
While BlackCat/ALPHV have not conducted the volume of attacks that counterparts like LockBit and more recently Cl0p can boast, they continue to have the most technically advanced RaaS platform offering and are continuing to and new capabilities.
First observed in late 2021, BlackCat/ALPHV employs a well-developed RaaS platform that encrypts by way of an AES algorithm. The code is highly customizable and includes JSON configurations for affiliate customization.
BlackCat/ALPHV released a new ransomware version called Sphynx with upgraded evasion capabilities. BlackCat/ALPHV can disable security tools and evade analysis and can employ several different encryption routines.
BlackCat/ALPHV was the first ransomware group to use Rust, a secure programming language that offers exceptional performance for concurrent processing. The ransomware deletes all Volume Shadow Copies using the vssadmin.exe utility and wmic to thwart rollback attempts and attains privilege escalation.
BlackCat/ALPHV developers opted for faster over stronger encryption by employing several modes of intermittent encryption and employs a tool called Exmatter for data exfiltration.
BlackCat/ALPHV has a wide variability in targeting, but most often focuses on the financial, manufacturing, legal and professional services industries and exfiltrates victim data prior to the execution of the ransomware – including from cloud-based deployments - to be leveraged in double extortion schemes to compel payment of the ransom demand.
The automation of network discovery to expand the range of addressable targets is also concerning. Automation means ransomware operators hit more victims faster, which translates to more ransoms collected and more fiscal pain for the victim organizations, which is the name of the game for these threat actors.
Halcyon.ai is the industry’s first dedicated, adaptive security platform that combines multiple advanced proprietary prevention engines along with AI models focused specifically on stopping ransomware – talk to a Halcyon expert today to find out more. And check out the Recent Ransomware Attacks resource site to get near real-time tracking of ransomware attacks, threat actor groups and their victims.
Related Posts
See Halcyon in action
Interested in getting a demo?
Fill out the form to meet with a Halcyon Anti-Ransomware Expert!





